DDoS is an abbreviation for the English name distributed denial-of-service and is far more dangerous than an ordinary denial of service attack. DDoS attacks often take out Web server or entire networks.
During a DDoS attack a website or an entire network are attacked by multiple computers at the same time. A failure of the server is mostly the consequence. Typically, DDoS attacker try to overload the access link, the firewall resources and, or the Web and database servers.
Thanks to the DDoS Protection at XiNiX powered by Arbor and Voxility at different locations; the analysis of the related traffic data is quickly. The traffic is adjusted by a cluster of filter systems, which is then transmitted to your server.

DDoS is a form of attack where a lot of zombie computers (infected computers that are under the control of the attacker) are used to either directly or indirectly to flood the targeted server(s) , victim, with a huge amount of information and choke it in order to prevent legitimate users from accessing them (mostly web servers that host websites).
In most cases, the owners of the zombie computers may not know that they are being utilized by attackers. In some cases, there is only a periodic flooding of web servers with huge traffic in order to degrade the service, instead of taking it down completely. On the diagram above you can see a typical DDoS Attack organization.
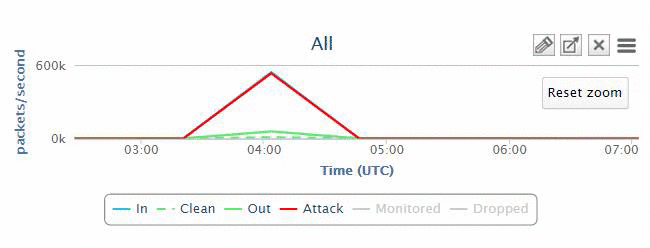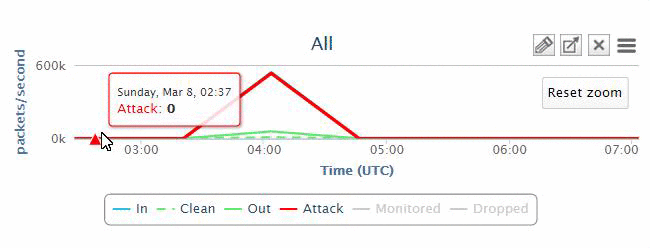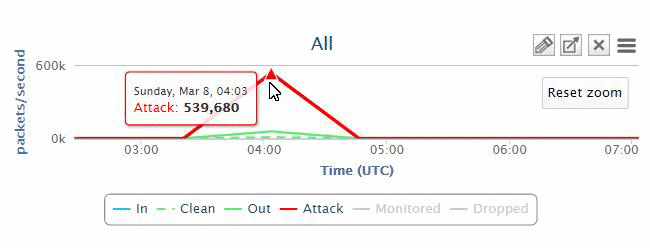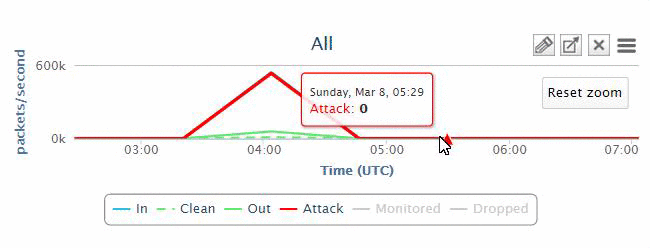
Hacker(s) sit at a remote terminal connected to a Botnet Control Centre, which in turn commands individual user machines, collectively called Botnet. These machines are compromised prior to the attack with special software that allows the hacker to exploit them. Subscribing to our service, you are protected from DDoS attacks, due to the fact that Bad/Attack traffic is directed to our protected network.
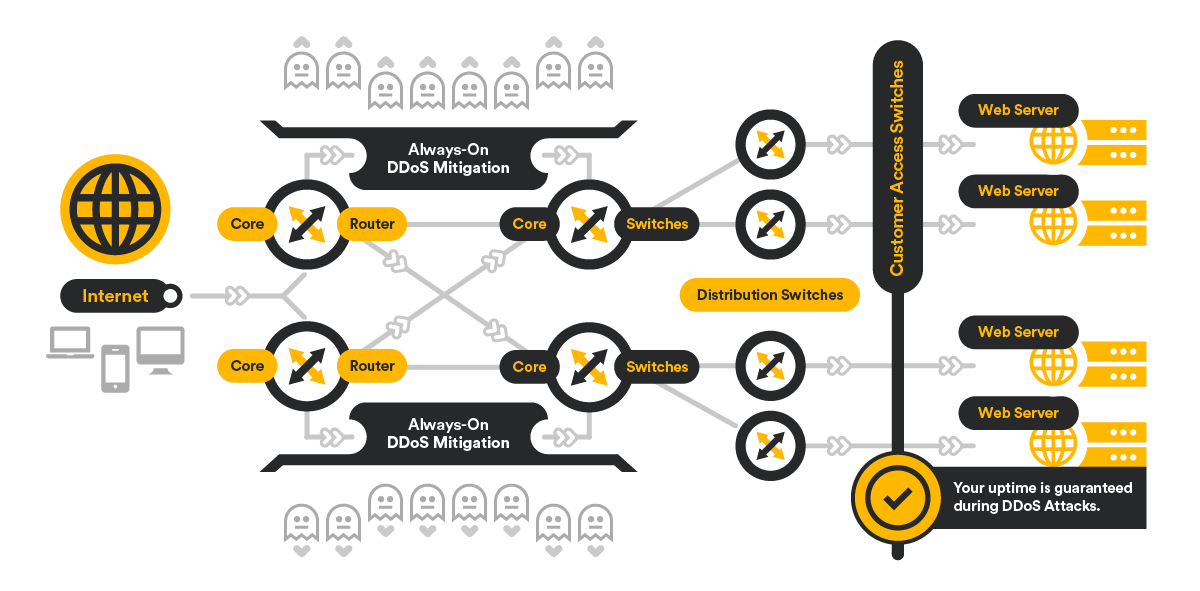
It consists of a number of Points of Presence (PoP) that we have around the world to ensure better connectivity with your visitors, allowing us to receive and balance malicious traffic globally.
See diagram below for schematics of one of our PoP's. When bad traffic reaches one of our PoP's it is being filtered and cleaned, then sent out to you as Clean traffic. Thus, your site's accessibility is ensured throughout the duration of any type of DDoS Attack.
To ensure proper and effective functioning of the filtering and cleaning processes in our PoP's, we have a Control Cluster, which monitors the work of the PoP's, analyses the issues and sends fresh and revised instructions as necessary.
In addition, we have Monitoring Points scattered throughout the globe, that report your site's status from real visitor locations. These also send information to the Control Cluster, thus effecting corrective action. With our industry-leading anti-DDoS hosting and mitigation best practices,
XiNiX™ provides online businesses with the most advanced DDoS protection available. Here at XiNiX™, we offer affordable, world-class DDoS protected hosting that simply cannot be compared to low-end budget providers. We may not be the least expensive, but we bundle in: free cPanel/WHM, free Email Pro, free Global Protected DNS, free backups, and high quality rockstar support.
XiNiX™'s broad portfolio of field-proven DDoS protected hosting solutions and industry-leading partnerships can keep your business safe from todays large and complex DDoS attacks, including the increasingly common high-bandwidth denial of service DDoS attacks that many DDoS protection providers struggle to mitigate.
All XiNiX™' servers come standard with 20 - 100 Gbps DDoS protection. Our DDoS protection utilizes our huge network of bandwidth providers, and we're able to quickly and effectively filter out packets. Activated automatically, you'll find that our DDoS protection isn't just easy to use, but you'll wonder how your business worked without it. The best part is that we'll never send an invoice for bandwidth overages if you've received a DDoS attack.
Our DDoS protection takes a three-pronged approach to solving the problem. First, we analyze the packets and ensure that we are not filtering legitimate traffic. Analysis is performed within 2 minutes of an attack starting, and the traffic passes through Arbor Peakflow boxes. Next, we clean the traffic. With our large network and multi-point DDoS protection, we are able to stop the traffic. Finally, we mitigate the traffic using our network firewalls and multi-point mitigation systems.